You must have heard about JSON web tokens abbreviated as JWT Token. It is a mechanism through which the client and server can trust each other and pass valuable information to each other. JWT is mostly used for Authentication and Authorization purposes. Let’s learn the details about the JSON Web Tokens
- Structure of JSON Web Token
- View the Details of the JSON Web Token
- Header of JSON Web Token
- Payload of JSON Web Token
- Signature of JSON Web Token
- How JWT Token is Safe and Secure
- References
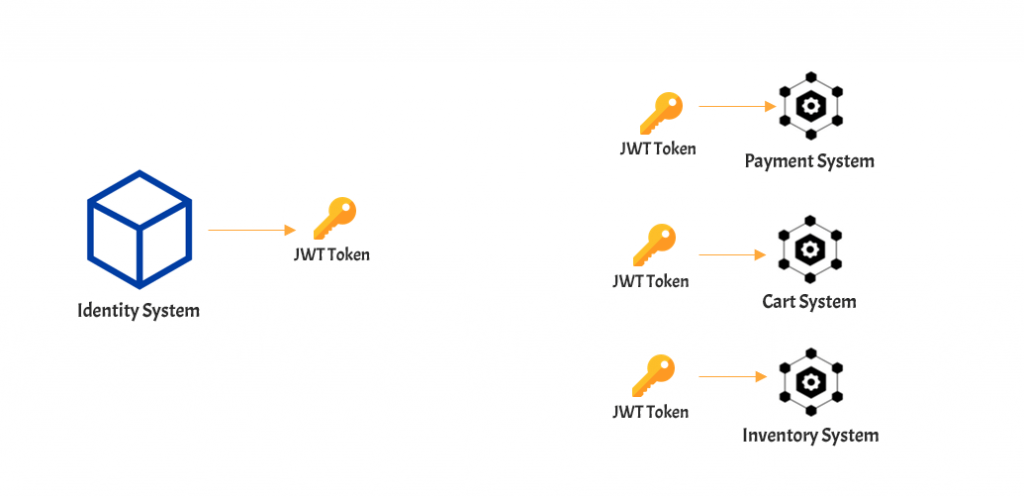
Structure of JSON Web Token
There are three parts of the JSON web token are
- Header
- Payload
- Signature
Each part is separated using a dot symbol. A typical JWT token can be represented below where XXXX is the header part, YYYY is the payload part and ZZZZ is the signature part
XXXX.YYYY.ZZZZA sample JSON Web Token is
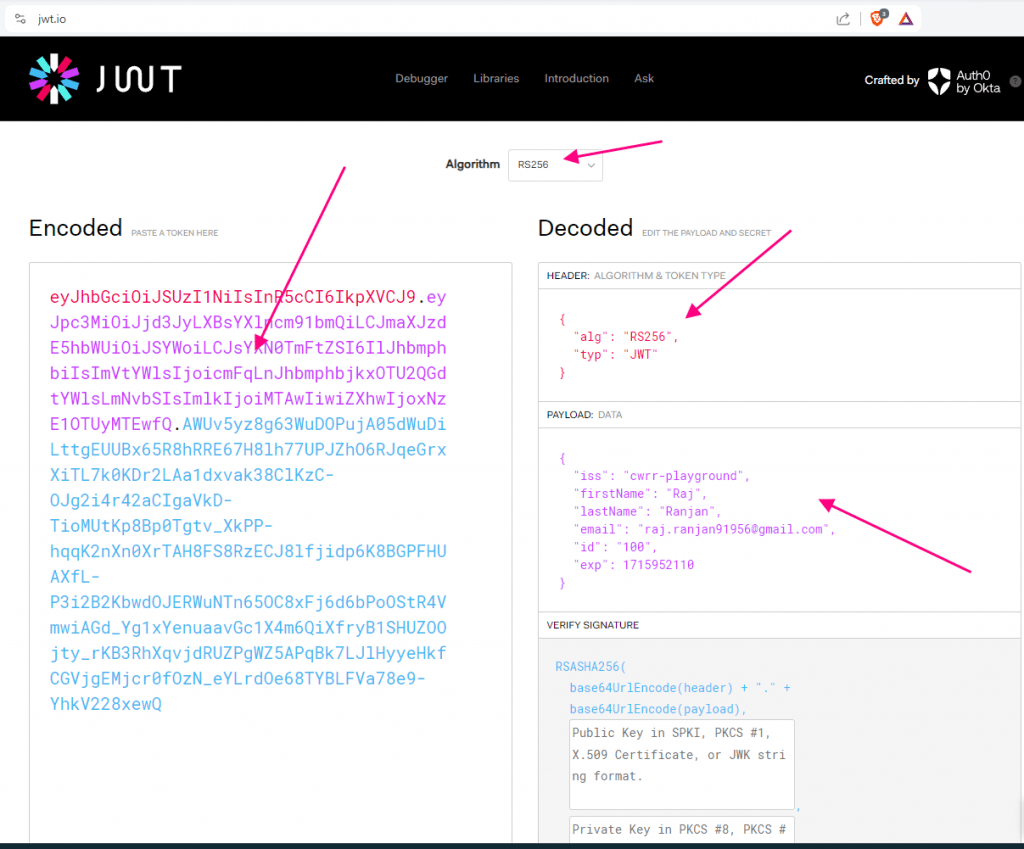
eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJjd3JyLXBsYXlncm91bmQiLCJmaXJzdE5hbWUiOiJSYWoiLCJsYXN0TmFtZSI6IlJhbmphbiIsImVtYWlsIjoicmFqLnJhbmphbjkxOTU2QGdtYWlsLmNvbSIsImlkIjoiMTAwIiwiZXhwIjoxNzE1OTUyMTEwfQ.AWUv5yz8g63WuDOPujA05dWuDiLttgEUUBx65R8hRRE67H8lh77UPJZhO6RJqeGrxXiTL7k0KDr2LAa1dxvak38ClKzC-OJg2i4r42aCIgaVkD-TioMUtKp8Bp0Tgtv_XkPP-hqqK2nXn0XrTAH8FS8RzECJ8lfjidp6K8BGPFHUAXfL-P3i2B2KbwdOJERWuNTn65OC8xFj6d6bPoOStR4VmwiAGd_Yg1xYenuaavGc1X4m6QiXfryB1SHUZOOjty_rKB3RhXqvjdRUZPgWZ5APqBk7LJlHyyeHkfCGVjgEMjcr0fOzN_eYLrdOe68TYBLFVa78e9-YhkV228xewQView the Details of the JSON Web Token
JWT token is a base64 encoded string. You can use the base64 decoder to view the details of the token. we will use an online tool to view the details of the token.
https://jwt.io/Open the website and paste the token in the encoded part. I will copy the above token and paste it there. You will see that when we put the JWT token in the encoded section then it gets converted to three parts on the right-hand side
- HEADER: Algorithm and Token Type
- PAYLOAD: DATA
- SIGNATURE
Header of JSON Web Token
{
"alg": "RS256",
"typ": "JWT"
}The header is the metadata for the token and mostly tells two things
- Type of the token. Token in our case is JWT (JSON Web Token)
- Algorithm used for signing of the token. The above token is signed using the RSA256 algorithm.
Different types of Algorithm can be used for signing the JWT token. They are mostly divided into two categories
- Symmetric Algorithm
- A single Key is used for both signing and verifying the token. For example the HMAC algorithm
- Asymmetric Algorithm
- Two different keys are used for signing and verifying the token. For example RSA256 Algorithm
- A Private Key is used for signing the token
- A Public key is used for verifying the token
Payload of JSON Web Token
{
"iss": "cwrr-playground",
"firstName": "Raj",
"lastName": "Ranjan",
"email": "raj.ranjan91956@gmail.com",
"id": "100",
"exp": 1715952110
}The Payload contains the data that will be shared between two different entities using the JWT token. It is mostly a key-value pair and is often referred to as claims in the JWT ecosystem.
You can pass as many claims as you want but you can also follow a standard using IANA JSON Web Token Registry or be defined as a URI that contains a collision-resistant namespace.
Some claims are not mandatory but are recommended to provide useful information and these are called registered claims.
- “iss” (Issuer) Claim: The entity that issued the JWT token. You can provide the name of the service that generated the JWT token.
- “sub” (Subject) Claim: The user for which the JWT token is generated. This can be a unique identifier for the user
- “exp” (Expiration Time) Claim: The “exp” (expiration time) claim identifies the expiration time on or after which the JWT MUST NOT be accepted for processing.
- “iat” (Issued At) Claim: The time at which the JWT was issued. This claim can be used to determine the age of the JWT.
Here in our JWT payload, we have provided important information about the user like ID, first name, last name, expiry time, etc
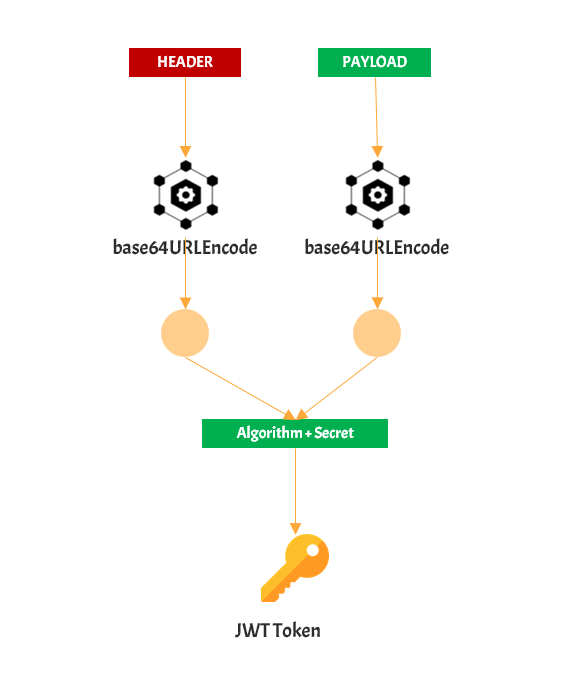
Signature of JSON Web Token
The signature is the unique value generated using the below things. Encoding is done using base64UrlEncode
- encoded header
- encoded payload,
- secret
- the algorithm specified in the header
How JWT Token is Safe and Secure
In a Symmetric Algorithm, the single private key will be used to sign and verify the token. If you tamper with the token, the signature will change and verification will fail. In a symmetric Algorithm, since the client will also have the same private key for verifying the token so using a single private is not safe.
In an Asymmetric Algorithm, we have different keys for signing and verifying the token. The private key is secure at the backed service. If you tamper with the token then the signature will change and the public key will fail the verification